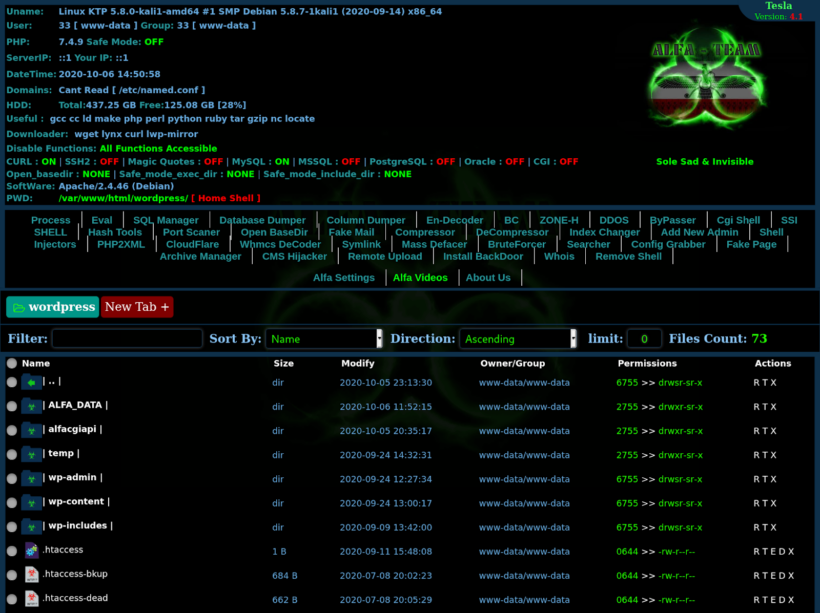
ALFA WEB SHELL | Bypass Alfa V4.1 Shell
Released in mid-September 2020 by the Iran-linked ALFA TEaM, this all-in-one PHP web shell lets attackers manage servers remotely, exfiltrate data, and launch phishing campaigns from a single panel. Compared with v3, the Tesla build widens its arsenal with dozens of one-click modules for database dumps, spam deployment, and CMS file management.
Three Stand-Out Features
1 Fakepage — Instant Phishing Page Builder
- Targets: cPanel or DirectAdmin log-in screens
- Clone: Copies the genuine login HTML instantly
- Inject To: Drops a single-line PHP redirect into the chosen file
- Bind On: Locks critical files like
wp-login.phpuntil the victim fails authentication three times - Log To: Stores captured credentials in plain-text
.txtfiles
In practice, the shell looks for ports :2083 (cPanel) or :2222 (DirectAdmin). A victim sees a perfect clone, tries to log in, fails, and their credentials are quietly logged before they reach the real panel.
2 Config_grabber — Low-Noise Config Theft
The Alfa_ConfigGrabber() routine sweeps directories for keywords such as DB_HOST and db_pass, ripping out database hostnames, usernames, and passwords in a single click. A greedy regex pulls in extra files, but attackers can still filter for the juicy bits with one more click.
3 Archive_manager — Memory-Only Extraction
Attackers upload a .zip or .tar.gz, then open it via the phar:// stream wrapper. Contents are browsed and executed in memory—nothing ever touches disk, dodging most log- and quota-based defenses.
How to Shrink Your Attack Surface
- Patch Early, Patch Often — Unpatched CMS cores and plugins are the #1 gateway for web shells.
- Enforce 2FA — Turn on two-factor authentication for cPanel / DirectAdmin and CMS logins.
- Run Server-Side Malware Scanning — Use a scanner that checks file integrity and flags unusual processes.
- Apply Least-Privilege Permissions — Limit PHP execute, read, and write rights on a per-file basis.
Conclusion
ALFA TEaM Shell v4.1-Tesla supercharges phishing, config harvesting, and stealthy archive handling—all from one dashboard. Beat it with proactive monitoring, timely patching, and strict access controls.